GIT - the risk of spoofing commits
 Image credit: Christina Morillo
Image credit: Christina MorilloSpoofing Git Commits in GitLab and GitHub
TL,DR: It is possible to commit to a git branch as any user. Both GitLab and GitHub will use the email address in the git commit as the user who pushed. This allows for any user to mimic any other user who’s email address is used for an account, and make it seem as if they pushed the code. The take away from this should be that your commits should be signed using ones PGP key.
Git feature or security problem
Using git one needs to add ones user name and email address:
git config user.email 'tests@example.com
git config user.name 'test'
This allows for the commit to be attributed to the one who did the commit even if they are not the ones who are pushing the code to the git server.
The issue that occurs in both GitLab and GitHub is that there is no distinction between the two. One can easily impersonate the commit as if it came from anyone else on the platform. Lets look at an example:
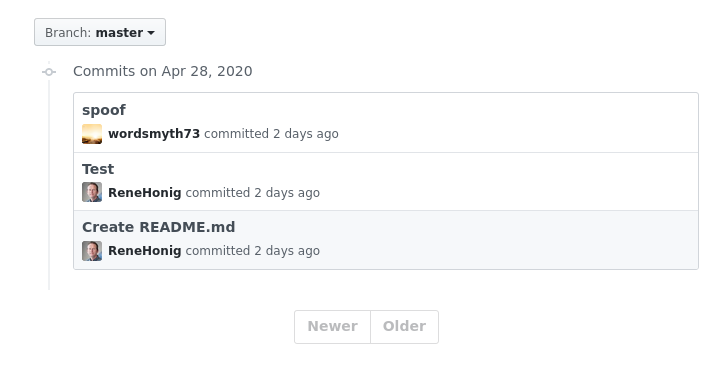
In the example above we can see the bottom commit is from the original owner. This is the original creator of the repo who has done a legitimate commit as themselves.
The second commit from the bottom however was done by another user who changed their
git config user.emailto be the original posters. The spoofed commit look like it if from the original owner but was actually never performed by them.The last commit is another spoofed commit however now the
git config user.emailwas replaced with another GitHub user who is not a member of this project. That user has never heard of this repo, nor ever wrote any ‘code’ for this project. It however now looks as if they are a contributer to this project. [0]
These all can be done by simply changing the git config user.email to any user who is on (in this case) GitHub. To be clear, to be able to perform this the spoofer still needs to have write access to the repository. But, a malicious user or disgruntled employ who already has write access to a repo could impersonate another individual to try and have code pushed through in someone else name. In both GitHub and GitLab there is no easy way to view if the commit matches with who pushed it. If one were to click on the user name for that commit it will go to the spoofed users profile. It would be nice to have a way to quickly see if a commit ‘identity’ matches the one who pushed the code.
[0] We did ask the user if we could use their account for this demonstration.
Securing against Spoofing
The best way to ensure that a commit is from a particular user is by enforcing that all commits be signed with a users PGP key. This can be easily dome by adding the -S during a commit git commit -S or by setting it as a global variable in ones .gitconfig using git config --global user.signingkey <KeyID>. A good example of how to get started is: GitLab PGP example.
It should also be set that particular branches (i.e. master) should only be committed to if the commit is properly signed. To do this on GitHub see the required commit signing.
It should be noted note that neither GitHub nor GitLab have done anything wrong here. They are both great tools that most of us use almost daily but it would be nice to have visual cue that the commit email does not match the user who pushed the code. This is a feature in git that can be used in a malicious manner.
